eSIMs are not a silver bullet. Like all tools, they come with trade-offs. For those working in complex environments or managing teams across geographies, it is important to understand where the benefits taper off and where digital risk may quietly creep in.
In Part 1, we looked at how eSIMs support mobility, cross-border access, and operational continuity. Here, we explore their limitations — and how to use them with intention, not assumption.
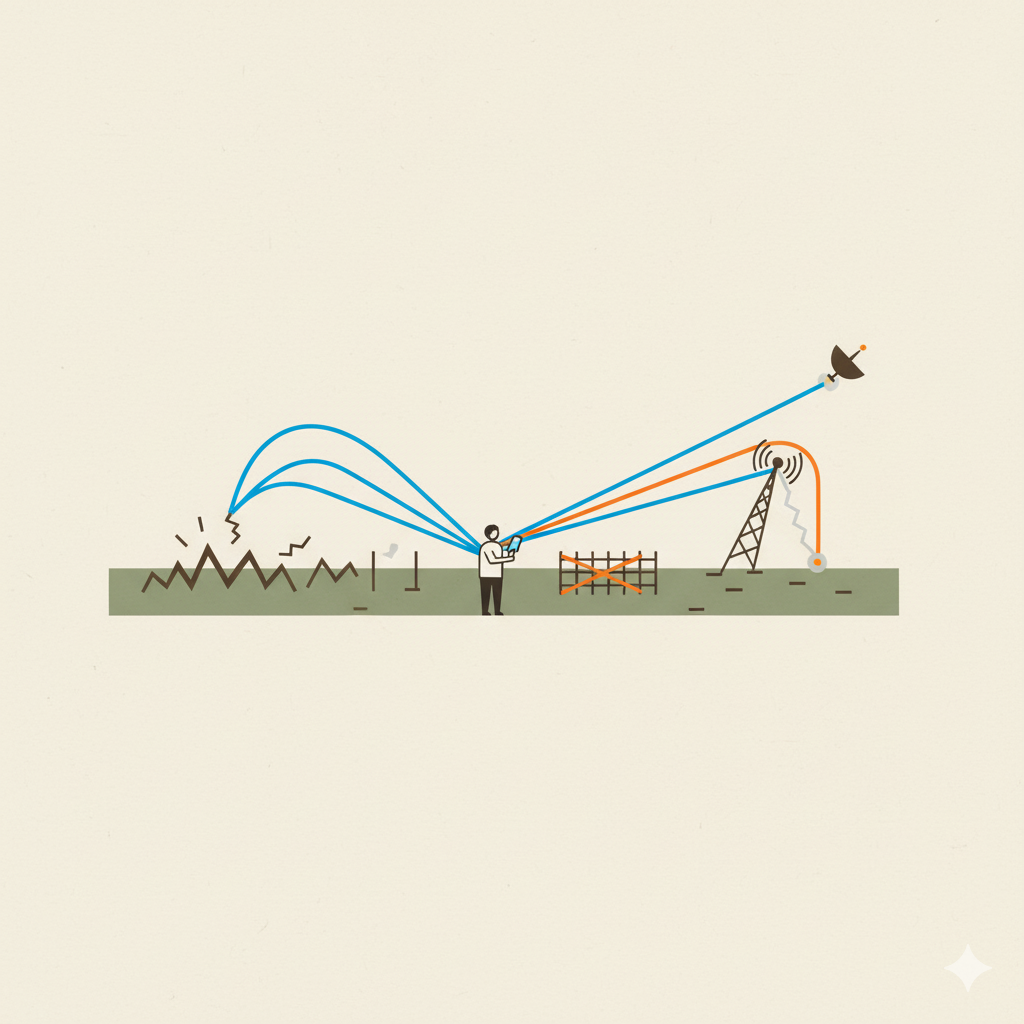
- eSIMs Still Rely on Local or Neighbouring Infrastructure
An eSIM does not replace the need for a functioning mobile network. If a country’s infrastructure is damaged, restricted, or switched off, an eSIM will still struggle to connect. It may, however, be able to pick up signal from across a nearby border.

We have seen field teams boost reception at fixed sites by repositioning routers or moving to known signal spots. In mobile operations, identifying zones where foreign towers regularly reach across can offer brief but vital digital windows. These are no substitute for full connectivity, but they are better than none.
- It Will Not Give You a Local Phone Number
Most eSIM packages for global travel offer data only. This means no voice calls or SMS, unless you use apps like WhatsApp, Signal, or Telegram. For many users this is enough, but for those who rely on local mobile numbers — for ID, access, or local services — a traditional SIM may still be needed.
We recommend considering eSIMs as part of a layered approach. Keep your physical SIM where it makes sense. Use eSIMs for travel, redundancy, or to avoid roaming fees. And wherever possible, pair your data use with a VPN.
- Local Providers May Offer Limited or No Support
In some countries, global eSIM providers may not have strong local partnerships. This can affect speed, stability, or even access. Worse, if your device is locked to a single carrier, or is incompatible with the eSIM standard, the service may fail altogether.

Before travelling, install the eSIM profile, run a speed test, and try switching providers within the eSIM app. Some services allow you to switch between multiple carriers in the same country — useful when one network becomes unstable.
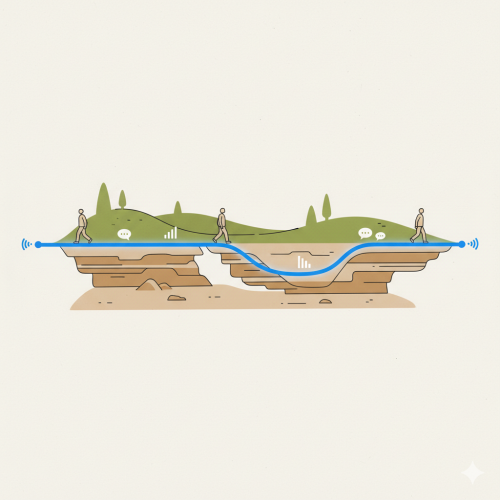
- Like Any Tech, It Can Fail — So Stay Practised
A common field reality: you become dependent on a tool, then lose access to it. eSIMs are convenient, but they do not replace radios, VSATs, physical SIMs, or local access points. If an app update breaks your connection, or a profile is deleted mid-mission, you need to know what to do next.
We encourage teams to train with their tools, run drills, and avoid defaulting to a single method of connectivity. An eSIM is a helpful fallback, but it should not be your only one.
- Using eSIMs Does Not Make You Secure
An eSIM is not a privacy tool. Anyone seeking to track a device does not need access to the SIM card. Phones can be located and exploited through a range of other methods — including Wi-Fi signals, GPS, Bluetooth, cookies, and app-level permissions.
Whether using an eSIM or not, users should avoid unprotected browsing, install updates cautiously, and limit sensitive communications over insecure apps. A VPN helps, but is not a cure-all. Devices, not SIMs, are the more likely risk surface.

Final Thought: Use It, But Use It Intentionally
An eSIM can offer real mobility advantages — especially in emergencies, stopovers, or regions with unstable providers. But like all communications tools, it works best when integrated into a broader strategy.
For those operating in field-based, cross-border, or mobile environments, we recommend keeping one or more eSIMs installed and ready to activate. They can be used as a primary access method, a fallback when local SIMs fail, or simply a cheaper way to manage short-term data.
Just remember: stay familiar with your settings, install before you go, and always keep more than one way to stay connected.
This article is part of a three-part series. In Part 3, we look at surveillance, data risk, and the broader implications of eSIM use in insecure or sensitive environments.
Want help setting up or boosting eSIM performance? We’ve supported field teams with eSIM configuration, signal boosting, and fallback planning. If you’d like a second pair of eyes on your setup, feel free to get in touch.